Quick Links:
Introduction
In recent years, the research directions of MobiTeC have extended beyond conventional telecommunications and networking to cover new application and service aspects of mobile technologies including mobile security, pervasive computing, Internet of Things, Cloud-based computing services, mobile/ online social networks and big data systems. Recent projects include:
- Vulnerability Analysis and Security Testing for Single-Sign-On Services in Mobile Applications. In particular, MobiTeC has designed and implemented a set of automated security testing tool/ services (MoSSOT and S3KVetter) for real-world Single-Sign-On (SSO) protocols such as OAuth2.0 and OpenID-Connect. Using these tools, we managed to conduct a large-scale investigation to analyze the security of the implementations of close to 1000 third-party websites/ mobile applications which used the SSO service provided by major Online Service Providers including Facebook, Google, Sina, Tencent, and Renren. Our investigation has discovered various new classes of critical SSO-related vulnerabilities which affected hundreds of millions of end-users world-wide. We have reported our findings and proposed fixes to all the affected identity providers/ developers and received their acknowledgements. Based on our suggestions, providers have also updated their SSO programming guide for third-party developers to explicitly explicate possible future misuses. Our technical findings were not only published as academic papers but also, presented in major industrial forums such as BlackHat and received extensive coverage by local, mainland and international media. Our work on the development of security vetting tools for Single-Sign-On Software Development Kits (SDKs) received the 2018 Internet Defense Prize from USENIX and Facebook.
- We have developed and continued to enhance the awarding-winning AuthPaper technology to meet the increasingly demanding and diverse requirements of supporting high-density, authenticated QR-codes for new secure, mobile/ pervasive computing applications. While the use of color in QR codes brings extra data capacity, it also inflicts new challenges on the decoding process due to chromatic distortion, cross-channel color interference and illumination variation. By introducing a new framework of High-capacity Color QR codes (HiQ) and novel algorithms to enable their robust and fast decoding, MobiTeC has developed and released an >open-source software platform to support HiQ codes generation as well as their fast and robust decoding. To further facilitate the benchmarking of color QR code decoding algorithms by researchers and practitioners world-wide, we have also created a large-scale color QR code dataset, CUHK-CQRC, and made it publicly available at http://www.authpaper.net/colorDatabase/index.html
- Due to the complex, multi-party trust relationship required by Mobile Payment Services, there is a high potential for massive cyber-security threats caused by improper implementation or lack of understanding/technical know-how amongst resource-constrained third party website or mobile application developers. By leveraging MobiTeC's world-class expertise in the security of Mobile Single-Sign-On (SSO) services, we have launched a new project to investigate the security of mobile payment protocols and systems in practice. We are also developing automated security testing tools for real-world mobile payment protocols, systems and applications.
- Another recent research direction of MobiTeC is on the empirical measurement, modeling and analysis of payment activities/ transactions among users of mobile social networking services. Topics under study include: community detection for mobile payment users, mobile-OSN-assisted credit/ trust evaluation and anomaly detection, the cultural and social aspects of online mobile payment activities etc.
Current Projects
|
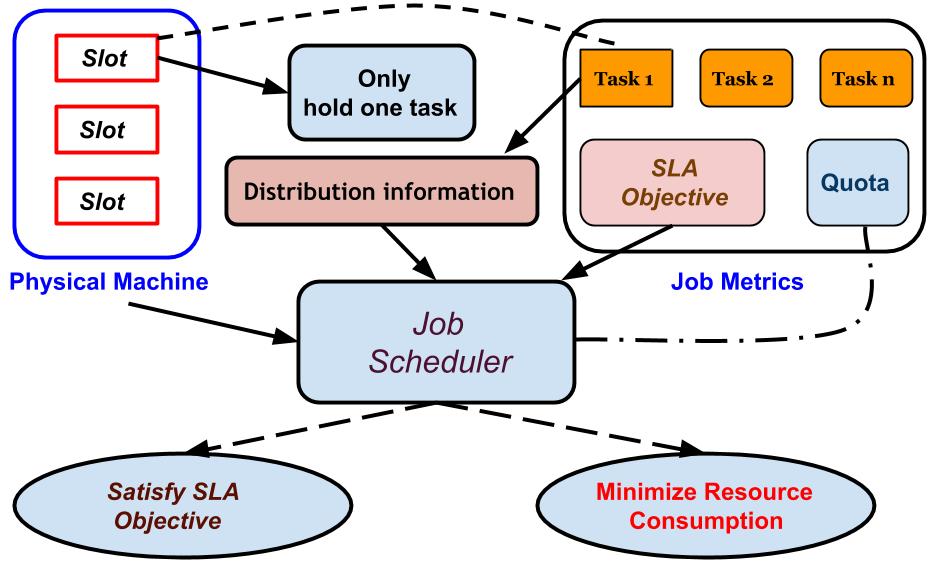
Resource Management and Job Scheduling in Cloud Computing
Cloud computing has emerged as an important computing paradigm. One critical issue is to guarantee the service quality for end users. To address this problem, we design smart algorithms in cloud computing environment to improve the performance of jobs submitted by users. At present, we mainly focus on two metrics of job which are completion time and resource consumption |
|
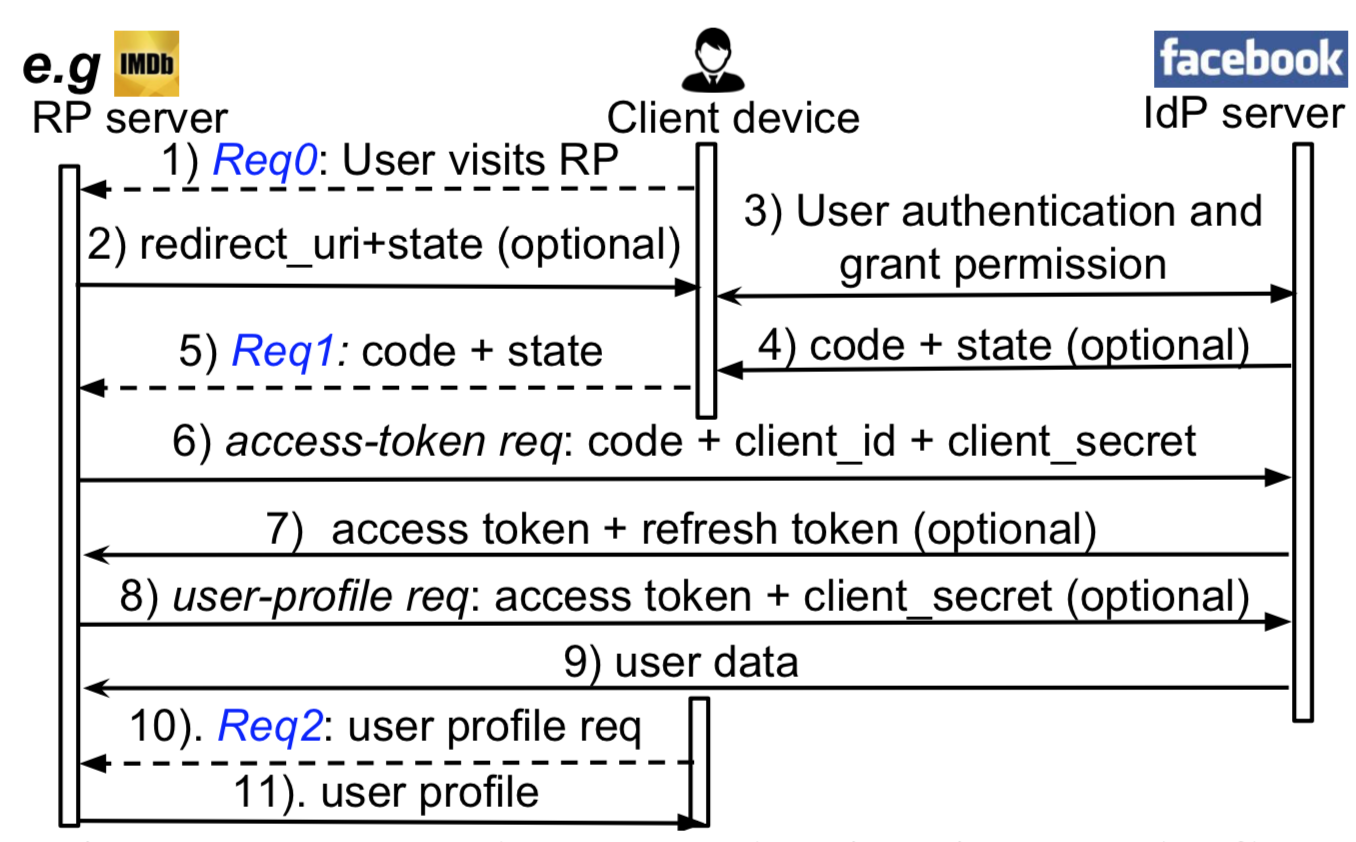
Single Sign On Security
Single Sign-On (SSO) protocols like OAuth2.0 and OpenID Connect have been widely adopted to simplify user authentication and service authorization for third-party applications. According to a survey, 75% users choose to use SSO services, instead of traditional passwords, to login applications. A conservative estimate shows 405 out of Top-1000 applications support SSO services, indicating that SSO login has already become a mainstream authentication method and still continues its strong adoption. These SDKs have become a critical foundation for web services. Despite its importance, little effort has been devoted to a systematic testing on the implementations of SSO SDKs, especially in the public domain. We study various topics related to Single Sign On security, trying to unveil security vulnerabilities during the SSO process. |

