Introduction
This page gives a quick introduction to PHYjacking. Details can be found in our NDSS'22 paper.
What is PHYjacking?
Mobile devices carry various hardware interfaces to facilitate human interaction, including touchscreen, camera, microphone, fingerprint scanner, etc. These interfaces are used by many mobile apps to read physical inputs from users for authorization purposes, such as one-click login, fingerprint payment, and face unlock. We take different hardware components and physical inputs into consideration and study the possibility of launching authorization hijacking attacks without special permissions on Android devices and propose a general attack framework called PHYjacking.
In short, we study the question raised in the following scenario:
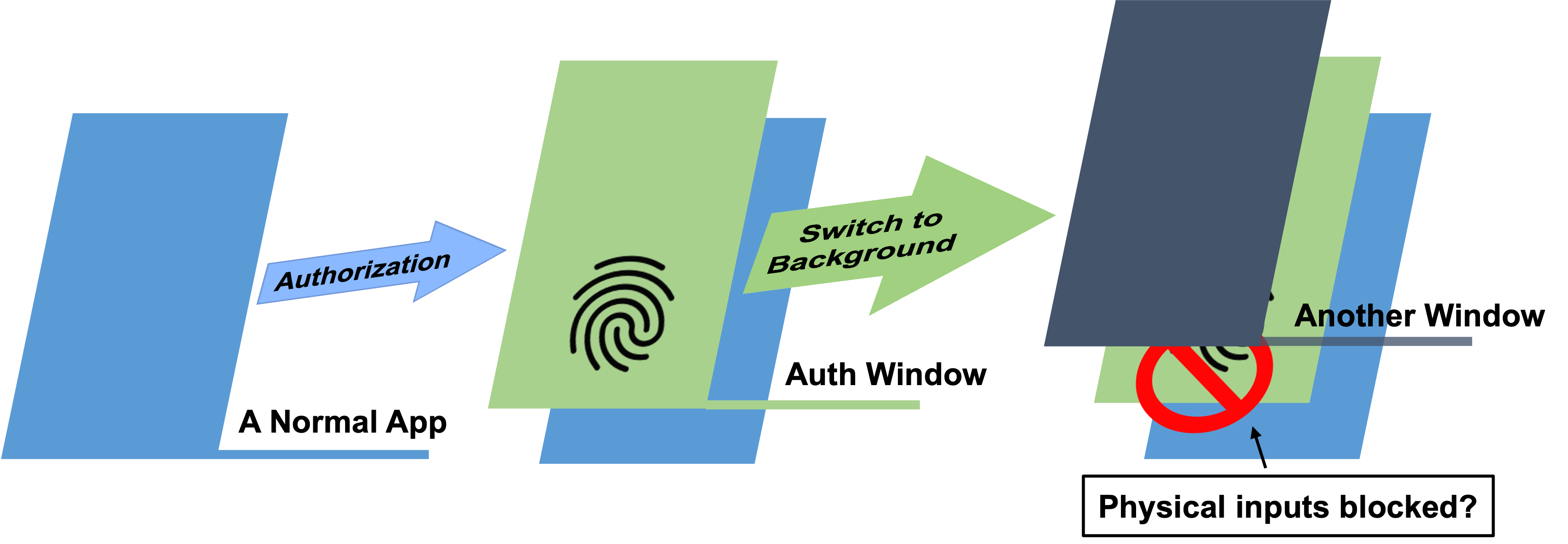
If the background app continues receiving user inputs like fingerprint scanning or face imaging during authorization, a malicious app can create a delusive covering to cause context confusion to the victim and lure for unwanted authorization.
We found that there are two cases where the background physical inputs are blocked:
- Android system interrupt the background sensor access to mitigate hijacking attacks.
- Apps cancel the input listener on specific Activity-lifecycle event, e.g.,
onPauseoronStop.
In either case, we identified security issues that can enable hijacking attacks, which leads to our discovery of variants of PHYjacking techniques.
PHYjacking Techniques
When clickjacking and tapjacking are common cases of PHYjacking, we also study hijacking attacks against other inputs available on modern mobile devices, including:
- Fingerprint-jacking: hijack fingerprint authorization/authentication with mobile fingerprint scanner.
- Facejacking: hijack face recognition with mobile camera.
- Voicejacking: hijack voice authentication with mobile microphone.
- NFC hijacking: hijack NFC card reading with mobile NFC reader.
We propose several attack techniques to achieve zero-permission and mitigation bypass, including:
- Translucent-attack: simplest attack - use translucent Activity as the malicious covering to attack apps containing incorrect sensor close implementation.
- Wakeup-bypass: perform confusion setup before device sleeps to bypass fingerprint hijacking mitigation added in Android 9.
- Multiwindow-bypass: perform confusion setup in the split window to bypass fingerprint hijacking mitigation added in Android 9.
- Race-attack: the most powerful attack which exploits a newly uncovered race condition bug in Android Acitivty-lifecycle management to break both app and system protections.
These PHYjacking techniques are summarized in the following figure. Details of each attack including Proof-of-Concept code and demo video can be found here.
Static Analyzer
Some of the PHYjacking techniques exploit improper implementation in Android apps. PHYjacking-checker is an open-source tool that can analyze APK packages statically and report whether apps contain potentially vulnerable implementations.
Responsible Disclosure
We have reported vulnerabilities we found in Android to Google and informed affected vendors. Google has released a patch against fingerprint-jacking in security patch level 2021-01-05 and the bug was assigned CVE-2020-27059.
Latest update
2022/04: Android team has confirmed that a new patch for the race-attack is ready and the vulnerability is reserved with CVE-2022-20007.